Beale ciphers
This article has multiple issues.Please helpimprove itor discuss these issues on thetalk page.(Learn how and when to remove these template messages)
|

TheBeale ciphersare a set of threeciphertexts,one of which allegedly states the location of a buriedtreasureof gold, silver and jewels estimated to be worth over 43 million US dollars as of January 2018.[update]Comprising three ciphertexts, the first (unsolved) text describes the location, the second (solved) ciphertext accounts the content of the treasure, and the third (unsolved) lists the names of the treasure's owners and theirnext of kin.
The story of the three ciphertexts originates from an 1885 pamphlet calledThe Beale Papers,detailing treasure being buried by a man named Thomas J. Beale in a secret location inBedford County, Virginia,in about 1820. Beale entrusted a box containing the encrypted messages to a local innkeeper named Robert Morriss and then disappeared, never to be seen again. According to the story, the innkeeper opened the box 23 years later, and then decades after that gave the three encrypted ciphertexts to a friend before he died. The friend then spent the next twenty years of his life trying to decode the messages, and was able to solve only one of them, which gave details of the treasure buried and the general location of the treasure. The unnamed friend then published all three ciphertexts in a pamphlet which was advertised for sale in the 1880s.
Since the publication of the pamphlet, a number of attempts have been made to decode the two remaining ciphertexts and to locate the treasure, but all efforts have resulted in failure.[1][2][3][4]
There are many arguments that the entire story is a hoax, including the 1980 article "A Dissenting Opinion" by cryptographerJim Gillogly,and a 1982 scholarly analysis of theBeale Papersand their related story byJoe Nickell,using historical records that cast doubt on the existence of Thomas J. Beale. Nickell also presents linguistic evidence demonstrating that the documents could not have been written at the time alleged (words such as "stampeding", for instance, are of later vintage). His analysis of the writing style showed that Beale was almost certainly James B. Ward, whose 1885 pamphlet brought the Beale Papers to light. Nickell argues that the tale is thus a work of fiction; specifically, a "secret vault" allegory of theFreemasons;James B. Ward was a Mason himself.[1]
Background
[edit]This sectionneeds additional citations forverification.(April 2024) |
A pamphlet published in 1885, entitledThe Beale Papers,is the source of this story. The treasure was said to have been obtained by an American named Thomas J. Beale in the early 1800s, from a mine to the north of Nuevo México (New Mexico), at that time in the Spanish province ofSanta Fe de Nuevo México(an area that today would most likely be part ofColorado). According to the pamphlet, Beale was the leader of a group of 30 gentlemen adventurers fromVirginiawho stumbled upon the rich mine of gold and silver while hunting buffalo. They spent 18 months mining thousands of pounds of precious metals, which they then charged Beale with transporting to Virginia and burying in a secure location. After Beale made multiple trips to stock the hiding place, he then encrypted three messages: the location, a description of the treasure, and the names of its owners and their relatives. The treasure location is traditionally linked toMontvaleinBedford County, Virginia.[citation needed]
Beale placed the ciphertexts and some other papers in an iron box. In 1822 he entrusted the box to aLynchburginnkeeper named Robert Morriss. Beale told Morriss not to open the box unless he or one of his men failed to return from their journey within 10 years.[citation needed]Sending a letter from St. Louis a few months later, Beale promised Morriss that a friend in St. Louis would mail thekeyto the cryptograms; however, it never arrived. It was not until 1845 that Morriss opened the box. Inside he found two plaintext letters from Beale, and several pages of ciphertext separated into Papers "1", "2", and "3". Morriss had no luck in solving the ciphers, and decades later left the box and its contents to an unnamed friend.[citation needed]
The friend, then using an edition of theUnited States Declaration of Independenceas the key for a modifiedbook cipher,successfully deciphered the second ciphertext which gave a description of the buried treasure.[citation needed]Unable to solve the other two ciphertexts, the friend ultimately made the letters and ciphertexts public in a pamphlet entitledThe Beale Papers,which was published by yet another friend, James B. Ward, in 1885.
Ward is thus not "the friend". Ward himself is almost untraceable in local records, except that a man with that name owned the home in which a Sarah Morriss, identified as the spouse of Robert Morriss, died at age 77, in 1863.[5]He also is recorded as becoming a Master Mason in 1863.[1]
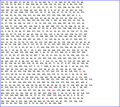
The images below, transcribed from the pamphlet, show the original line-breaks for easy comparison. In the second cryptogram, the original cipher errors are highlighted in red.
-
Beale's first cryptogram
-
Beale's second cryptogram (the deciphered one)
-
Beale's third cryptogram.
Deciphered message
[edit]This articlepossibly containsoriginal research.(April 2024) |
Theplaintextof paper number 2 reads:
I have deposited in the county of Bedford, about four miles from Buford's, in an excavation or vault, six feet below the surface of the ground, the following articles, belonging jointly to the parties whose names are given in number three, herewith:
The first deposit consisted of ten hundred and fourteen pounds of gold, and thirty-eight hundred and twelve pounds of silver, deposited Nov. eighteen nineteen. The second was made Dec. eighteen twenty-one, and consisted of nineteen hundred and seven pounds of gold, and twelve hundred and eighty-eight of silver; also jewels, obtained in St. Louis in exchange to save transportation, and valued at thirteen thousand dollars.
The above is securely packed in iron pots, with iron covers. The vault is roughly lined with stone, and the vessels rest on solid stone, and are covered with others. Paper number one describes the exact locality of the vault, so that no difficulty will be had in finding it.
The second cipher can be decrypted fairly easily using a modified copy of theUnited States Declaration of Independence,but some editing is necessary.[citation needed]To decrypt it, one finds the word corresponding to the number (e.g., the first number is 115, and the 115th word in the Declaration of Independence is "instituted" ), and takes the first letter of that word (in the case of the example, "I" ).
Beale used a version of the United States Declaration of Independence slightly different from the original, and made mistakes in numbering it.[citation needed]To extract the hidden message, the following five modifications must be applied to the original text:
- after word 154 ( "institute" ) and before word 157 ( "laying" ), one word must be added. The pamphlet handles this by inserting "a" before "new government".[6]
- after word 240 ( "invariably" ) and before word 246 ( "design" ), one word must be removed (probably "a" ). The pamphlet's numbering has eleven words between the labels for 240 and 250.[6]
- after word 466 ( "houses" ) and before word 495 ( "be" ), ten words must be removed (probably "He has refused for a long time after such dissolutions" ). The pamphlet has two labels for 480.[7]
- after word 630 ( "eat" ) and before word 654 ( "to" ), one word must be removed (probably "the" ). The pamphlet's numbering has eleven words between the labels for 630 and 640.[7]
- after word 677 ( "foreign" ) and before word 819 ( "valuable" ), one word must be removed (probably "their" ). The pamphlet's numbering has eleven words between the labels for 670 and 680.[7]
Furthermore:
- Words 78 and 79 ( "self-evident" ), shown hyphenated, are counted as two words.
- The first letter of word 95 ( "inalienable" ) is always used as a "u" ( "unalienable" ).
- Words 509 and 510 of the modified text ( "mean time" ) are counted as two words, despite being shown as one word.
- The first letter of the 811th word of the modified text ( "fundamentally" ) is always used by Beale as a "y".
- The first letter of the 1005th word of the modified text ( "have" ) is always used by Beale as an "x".
Finally, in the decoded text there are six errors, probably due to wrong transcription of the original paper:[citation needed]
- ... 84, 57, 540, 217, 115, 71, 29, 84 (should be 85), 63,...consistcd( "consisted" ).
- ... 53 (should be 54), 20, 125, 371, 38, 36, 10, 52,...rhousand( "thousand" ).
- ... 2, 108 (should be 10, 8), 220, 106, 353,...itron( "in iron" ).
- ... 440 (should be 40), 370, 643, 466,...uith( "with" ).
- ... 14, 73, 84 (should be 85),...thc( "the" ).
- ... 807, 81, 96 (should be 95), 405, 41,...varlt( "vault" ).
Additional Declaration differences affect paper number 1: word 210 of the modified text ( "more" ) is shown as "now"; words 919 and 920 of the modified text ( "fellow citizens" ) are shown hyphenated (also affects paper number 3); two extra words ( "made" and "the" ) are shown in modified text positions 1058 and 1188; a word is removed ( "of" ) after modified text position 1125. The other slight changes probably have no consequences.
Many versions of the Declaration of Independence have been printed, with various adjustments to paragraphing, word inclusion, word changing, spelling, capitalization, and punctuation.[citation needed]
The lack of clear images of the original ciphers, combined with the large quantity of numerals, has led to numerals being misprinted or omitted in many sources.
The Beale Papers text, on pages 20 to 21, gives an alleged translation of the second ciphertext, but it has nine differences from the actual one. The differences are shown here as {alleged decipherment | actual decipherment}:
I have deposited, in the county of Bedford, about four miles from Buford's, in an excavation or vault, six feet below the surface of the ground, the following articles, belonging jointly to the parties whose names are given in number { “3,” | three} herewith:
The first deposit consisted of {one thousand | ten hundred} and fourteen pounds of gold, and {three thousand | thirty-} eight hundred and twelve pounds of silver, deposited {November, 1819 | Nov. eighteen nineteen}. The second was made {December, 1821 | Dec. eighteen twenty-one}, and consisted of nineteen hundred and seven pounds of gold, and twelve hundred and eighty-eight {pounds | } of silver; also jewels, obtained in St. Louis in exchange {for silver | } to save transportation, and valued at {$13,000 | thirteen thousand dollars}.
The above is securely packed in iron pots, with iron covers. The vault is roughly lined with stone, and the vessels rest on solid stone, and are covered with others. Paper number { “1” | one} describes the exact locality of the vault, so that no difficulty will be had in finding it.
Value
[edit]The treasure's total weight is about 3tonsas described in inventory of the second cryptogram. This includes approximately 35,052troy ozgold, 61,200 troy oz silver (worth aboutUS$42million andUS$1million, respectively, in January 2017[8]) and jewels worth aroundUS$220,000in 2017.
Authenticity
[edit]There has been considerable debate over whether the remaining two ciphertexts are real orhoaxes.An early researcher, Carl Hammer ofSperry UNIVAC,[9]usedsupercomputersof the late 1960s to analyze the ciphers and found that while the ciphers were poorly encoded, the two undeciphered ones did not show the patterns one would expect of randomly chosen numbers and probably encoded an intelligible text.[10]Other questions remain about the authenticity of the pamphlet's account.
The pamphlet's background story has several implausibilities, and is based almost entirely oncircumstantial evidenceandhearsay.
- Latercryptographershave claimed that the two remaining ciphertexts have statistical characteristics which suggest that they are not actually encryptions of an English plaintext.[11][12]Alphabetical sequences such asabcdefghiijklmmnohppare both non-random, as indicated by Carl Hammer,[10]and not words in English.
- Others have also questionedwhyBeale would have bothered writing three different ciphertexts (with at least two keys, if not ciphers) for what is essentially a single message in the first place,[13]particularly if he wanted to ensure that the next of kin received their share (as it is, with the treasure described, there is no incentive to decode the third cipher).[10]
- Analysis of the languageused by the author of the pamphlet (the uses of punctuation, relative clauses, infinitives, conjunctives, and so on) has detected significant correlations between it and the writing style of Beale's letters, including the plaintext of the second cipher, suggesting that they may have been written by the same person.[1]
- The letters also contain several English words, such as "improvise", not otherwise recorded before the 1820s in English[14]but used from French from 1786 in the New Orleans area,[15]andstampede(Spanish) "an uproar".[16]Beale's "stampeding" apparently first appears in print in the English language in 1832[17]but was used from 1786 to 1823 in New Orleans in French and Spanish.[1]
- The second message, describing the treasure, has been deciphered, but the others have not, suggesting a deliberate ploy to encourage interest in deciphering the other two texts, only to discover that they are hoaxes. In addition, the original sale price of the pamphlet, 50 cents, was a high price for the time (adjusted forinflation,it is equivalent to $16.96 today[18]), and the author writes that he expects "a wide circulation".
- The third cipher appears to be too short to list thirty individuals' next of kin.[10]
- If the modified Declaration of Independence is used as a key for the first cipher, it yields Alpha betical sequences such asabcdefghiijklmmnohpp[19]and others. According to theAmerican Cryptogram Association,the chances of such sequences appearing multiple times in the one ciphertext by chance are less than one in a hundred million million.[19]Although it is conceivable that the first cipher was intended as aproof of conceptletting decoders know that they were "on the right track" for one or more of the subsequent ciphers, such a proof would be redundant, as the success of the key with respect to the second document would provide the same evidence on its own.
- Robert Morriss, as represented in the pamphlet, says he was running the Washington Hotel in 1820, yet contemporary records show he did not start in that position until at least 1823.[20]
- In fact a commonliterary deviceof fiction is the story of finding a lost treasure map from Edgar Allan Poe's "The Gold-Bug"to Robert Louis Stevenson'sTreasure Islandto Milton Caniff'sTerry and the Pirates.
There have been many attempts to break the remaining cipher(s). Most attempts have tried other historical texts as keys (e.g.,Magna Carta,various books of theBible,theU.S. Constitution,and the Virginia Royal Charter), assuming the ciphertexts were produced with some book cipher, but none have been recognized as successful to date. Breaking the cipher(s) may depend on random chance (as, for instance, stumbling upon a book key if the two remaining ciphertexts are actually book ciphers); so far, even the most skilledcryptanalystswho have attempted them have been defeated. Of course, Beale could have used a document that he had written himself for either or both of the remaining keys or either a document of his own or randomly selected characters for the third source, in either case renderinganyfurther attempts to crack the codes useless.
Existence of Thomas J. Beale
[edit]A survey ofU.S. Censusrecords in 1810 shows two persons named Thomas Beale, in Connecticut and New Hampshire. However, the population schedules from the 1810 U.S. Census are completely missing for seven states, one territory, the District of Columbia, and 18 of the counties of Virginia.[21]The 1820 U.S. Census has two persons named Thomas Beale, Captain Thomas Beale of the battle of New Orleans 1815 in Louisiana originally from Virginia Botetourt County – Fincastle area 12 miles from Bedford County and one in Tennessee, and a Thomas K. Beale in Virginia, but the population schedules are completely missing for three states and one territory.
Before 1850 the U.S. Census recorded the names of only the heads of households; others in the household were only counted. Beale, if he existed, may have been living in someone else's household.[22]
In addition, a man named "Thomas Beall" appears in the customer lists of St. Louis Post Department in 1820. According to the pamphlet, Beale sent a letter from St. Louis in 1822.[19]
Additionally, a Cheyenne legend exists about gold and silver being taken from the West and buried in mountains in the East, dating from roughly 1820.[19]
Poe's alleged authorship
[edit]Edgar Allan Poehas been suggested[by whom?]as the pamphlet's real author because he had an interest in cryptography. It was well known he placed notices of his abilities in thePhiladelphiapaperAlexander's Weekly (Express) Messenger,inviting submissions of ciphers which he proceeded to solve.[23]In 1843 he used a cryptogram as aplot devicein his short story "The Gold-Bug".From 1820, he was also living inRichmond, Virginiaat the time of Beale's alleged encounters with Morriss. In February 1826, Poe enrolled as a student at theUniversity of VirginiainCharlottesville,[24]but with mounting debts, Poe left forBostonin April 1827.[25]
However, research and facts debunk Poe's authorship. He died in 1849, well beforeThe Beale Paperswere first published in 1885. The pamphlet also mentions theAmerican Civil Warthat started in 1861.William Poundstone,an American author and skeptic, hadstylometric analysisperformed on the pamphlet for his 1983 bookBiggest Secrets,and found that Poe'sproseis significantly different from thegrammatical structureused by the author who wroteThe Beale Papers.[26]
Statistical analysis
[edit]Another method to check the validity of the ciphers is to investigate some statistical aspects in different number bases. For example, one can investigate the frequency of the last digit in each number in the ciphers. These frequencies are not uniformly distributed – some digits are more common than others. This is true for all three ciphers.[27]
However, if one considers a base that is relatively prime to 10, then the last digits of the numbers in the unsolved ciphers turn uniform – each digit is equally common. The frequency of the solved cipher stays non-uniform. This indicates a complex behaviour in the solved cipher as one might expect from an encoded message, while the unsolved ciphers have a simpler behaviour.[original research?]
Humans have limited abilities when it comes to generating random numbers out of thin air.[28]One explanation for the difference between base 10 and the other ones is that the numbers were produced by a human in base 10, which would mean that the ciphers are fraudulent.

Search attempts
[edit]Despite the Beale Papers' unproven veracity, treasure hunters have not been deterred from trying to find the vault. The "information" that there is buried treasure in Bedford County has stimulated many expeditions with shovels, and other implements of discovery, looking for likely spots.[citation needed]For more than a hundred years, people have been arrested for trespassing and unauthorized digging; some of them in groups as in the case of people from Pennsylvania in the 1990s.[19]
Several digs were completed at the top of Porter's Mountain, one in the late 1980s with the land owner's permission as long as any treasure found was split 50/50. However, the treasure hunters found onlyCivil Warartifacts. As the value of these artifacts paid for time and equipment rental, the expedition broke even.[19]
Media attention
[edit]The story has been the subject of multiple television documentaries, such as the UK'sMysteriesseries, a segment in the seventh special ofUnsolved Mysteries;and the 2011Declaration of Independenceepisode of the History Channel TV showBrad Meltzer's Decoded.There are also several books, and considerable Internet activity. In 2014, theNational GeographicTV showThe Numbers Gamereferred to the Beale ciphers as one of the strongest passwords ever created. In 2015 theUKTVseriesMyth Hunters(also known asRaiders of the Lost Past) devoted one of its season 3 episodes to the topic.[citation needed]Also in 2015, theJosh GatesseriesExpedition Unknownvisited Bedford to investigate the Beale Ciphers and search for the treasure.
Simon Singh's 1999 bookThe Code Bookexplains the Beale cipher mystery in one of its chapters.[19]
In 2010, an award-winning animated short film was made concerning the ciphers calledThe Thomas Beale Cipher.[29]
See also
[edit]- List of ciphertexts
- Rennes-le-Château– a similar case where encrypted documents, discovered in a church in France, allegedly refer to a hidden treasure
- Oak Island mystery– an alleged undiscovered buried treasure on Oak Island in Nova Scotia
- Captain Kidd– a 17th-century pirate who is supposed to have left behind clues to buried treasure
- Treasure of Lima– another legendary lost treasure
- Lost Dutchman's Gold Mine– legendary lost treasure
References
[edit]- ^abcdeNickell, Joe (July 1982). "Discovered: The secret of Beale's treasure".The Virginia Magazine of History and Biography.90(3): 310–324.JSTOR4248566.
- ^"The Beale Treasure Ciphers".The Guardian.1999. Archived fromthe originalon 2006-12-30.Retrieved2007-04-14.
- ^Dunin, Elonka(2003-12-08)."Famous Unsolved Codes and Ciphers".Archivedfrom the original on 23 April 2007.Retrieved2007-04-14.
- ^Burchard, Hank (5 May 1972)."Leading cryptanalysts seek to break secret code reported to tell of buried treasure in Virginia"(PDF).The Washington Post.
- ^"Sarah Morriss". obituary.Lynchburg Virginian.21 May 1865.
- ^ab"The Beale Papers, page 17".wikisource.org.Retrieved22 April2021.
- ^abc"The Beale Papers, page 18".wikisource.org.Retrieved22 April2021.
- ^"Historical London Fix Prices Current Year| Kitco".kitco.RetrievedMay 13,2020.
- ^Burchard, Hank (7 September 1979)."Motley group gathers to solve ciphers to treasure".The Washington Post.
- ^abcdPoundstone, William(1993).Biggest Secrets.New York, NY:William Morrow and Company.p.127.ISBN0-688-11529-2.
- ^Gillogly, James(April 1980)."The Beale Cipher: A Dissenting Opinion".Cryptologia.Archived fromthe originalon 26 January 2006.
- ^Love, George (20 April 2006)."The Beale Ciphers".Archived fromthe originalon 20 April 2006.
- ^Kruh, Louis (October 1982)."A basic probe of the Beale Cipher as bamboozlement"(PDF).Cryptologia.
- ^"Improvise".The New Monthly Magazine and Literary Journal.Vol. 12. 1824.
- ^Harper, Douglas."improvisation".Online Etymology Dictionary.
- ^Harper, Douglas."stampede".Online Etymology Dictionary.
- ^Sherwood, Mary Elizabeth Wilson (1834).Etiquette, the American Code of Manners.G. Routledge & Sons. p. 107.
- ^1634–1699:McCusker, J. J.(1997).How Much Is That in Real Money? A Historical Price Index for Use as a Deflator of Money Values in the Economy of the United States: Addenda et Corrigenda(PDF).American Antiquarian Society.1700–1799:McCusker, J. J.(1992).How Much Is That in Real Money? A Historical Price Index for Use as a Deflator of Money Values in the Economy of the United States(PDF).American Antiquarian Society.1800–present:Federal Reserve Bank of Minneapolis."Consumer Price Index (estimate) 1800–".RetrievedFebruary 29,2024.
- ^abcdefgSingh, S (2000).The Code Book.Fourth Estate. p. 97.ISBN1-85702-889-9.
- ^Poundstone, 127–128.
- ^Murphy, Linda Troutt (25 July 2006)."Missing Federal Census Schedules".Traut / Trout(t) Family.Archived fromthe originalon 13 January 2009.
- ^"Clues in Census Records, 1790–1840".National Archives and Records Administration. Archived fromthe originalon 19 July 2006.
- ^Silverman, Kenneth(1991).Edgar A. Poe: Mournful and Never-Ending Remembrance(Paperback ed.). New York: Harper Perennial. p.152.ISBN978-0-06-092331-0.
- ^Poundstone, 126.
- ^Meyers, Jeffrey (1992).Edgar Allan Poe: His Life and Legacy(Paperback ed.). New York: Cooper Square Press. p. 32.ISBN978-0-8154-1038-6.
- ^Poundstone, 133.
- ^Wase, Viktor (2020)."The Role of Base 10 in the Beale Papers"(PDF).Proceedings of the 3rd International Conference on Historical Cryptology HistoCrypt 2020.Vol. 171. pp. 153–157.doi:10.3384/ecp2020171019.ISBN978-91-7929-827-2.S2CID219488310.
- ^Wagenaar, W. A. (1972)."Generation of random sequences by human subject: A critical survey of literature"(PDF).Psychological Bulletin.77:65–72.doi:10.1037/h0032060.
- ^"The Thomas Beale Cipher: A Short Film by Andrew Allen".thomasbealecipher.RetrievedMay 13,2020.
Further reading
[edit]- Viemeister, Peter.The Beale Treasure: New History of a Mystery,1997. Published by Hamilton's, Bedford, Virginia
- Gillogly, James J."The Beale Cipher: A Dissenting Opinion April 1980Cryptologia,Volume 4, Number 2
- Easterling, E.J.In Search Of A Golden Vault: The Beale Treasure Mystery( CD/AUDIO BOOK 70 min. ) copyright 1995/ Revised In 2011. Avenel Publishing 1122 Easter Lane Blue Ridge, VA 24064.
External links
[edit]- "The Beale Papers on Wikisource".,as text in separate pages, shown alongside images of the original.
- "The Beale Papers".YouTube.Archivedfrom the original on 2021-12-12.have been made in video format with audio for the whole pamphlet.
- "The legendary Beale treasure".
- "The making of" Mysteries "".
- "The Quest to Break America's Most Mysterious Code – And Find $60 Million in Buried Treasure".4 June 2018.
- The Thomas Beale CipheratIMDb
- Dunning, Brian(March 13, 2012)."Skeptoid #301: The Beale Ciphers".Skeptoid.
- "Historical and Analytical Studies in Relation to the Beale Ciphers"